What is Trojan Horse (in Computing) ?
Trojan horses or better known as Trojans in computer security refers to a malicious software that can damage a system or network. The purpose of the Trojan is to get information from the target (passwords, user habits recorded in system logs, data, etc.), and control the target (gain permissions on the target). Unlike computer viruses and worms, Trojans generally do not attempt to inject themselves into other files or otherwise propagate themselves. Trojans are "stealth" (invisible) in operation and often shaped as if the program is a good program, while computer viruses or worms act more aggressively by destroying the system or causing the system to crash.
Kontributor :
Salma Fida. H
What are the types of trojans?
- Password thief. This Trojan type can search for passwords stored in the operating system (/ etc / passwd or / etc / shadow in the UNIX operating system family or the Security Account Manager (SAM) file in the Windows NT operating system family) and send it to the the original attacker. In addition, this type of Trojan can also deceive the user by making the display as if he / she is the login screen (/ sbin / login in UNIX or Winlogon.exe operating system in the Windows NT operating system) and waiting for the user to enter his password and send it to the attacker. An example of this type is the Passfilt Trojan that acts as if it is a Passfilt.dll file originally used to add password security in the Windows NT operating system, but is misused as a password stealer program.
- keystroke logger/keylogger. This Trojan type will monitor everything typed by the user and will send it to the attacker. This type is different from spyware, although the two things do the same thing (spying on the user).
- Remote Administration Tools/RAT. This type of Trojan allows attackers to take full control of the system and do whatever they want remotely, such as formatting the hard disk, stealing or erasing data and so on. Examples of these Trojans are Back Orifice, Back Orifice 2000, and SubSeven.
- DDoS Trojan or Zombie Trojan. This Trojan type is used to infect an infected system in order to perform distributed denial of service attacks against the target host.
- Cookies Stuffing, this is a script that is included in the blackhat method, the point is to hijack the tracking code sales of a product, so the sales commission accepted by the installer of cookies stuffing, not by the person who first refer the sale of the product on the internet
Who is the maker of Trojans?
The maker of Trojans isn’t known, even the makers of trojan horse virus itself will not tell what inspired them when making a Trojan horse virus, but this Trojan horse virus is highly avoided by computer users both male and female because of the Trojan horse virus is a program that looks fine from outside it turns in it keeps the intent - the intent of evil like stealing passwords, control the computer remotely and others.
Why is trojan created?
As usually a virus was created to take over a computer and use it for a specific purpose, steal sensitive information (passwords, personal details, data etc.), disable computers or networks, etc.
What are the signs we hit by a Trojans?
- When visiting a site, there are several pop-ups appearing and have visited one of the pop-ups. However, when it will end the visit (not fully visited), the browser suddenly redirects and unlocks some unknown pages.
- Unknown display of mailboxes appears on the screen. Messages containing some questions are private.
- The Windows view changes itself. For example, new screensaver text, date / time, volume change sound by itself, mouse pointer moves by itself, CD-ROM drive opens and closes itself.
- Outlet Express takes a long time to close (close) or look hang (hang) when viewing preview.
- The existence of damaged or missing files.
- An unknown program is actively visible in the task list.
- Signs or information from the firewall about outbound communications from unknown sources.
How to detect and clean from Trojans?
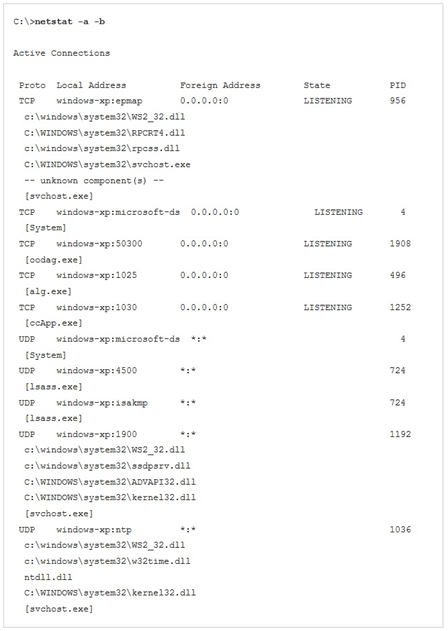
- Checking Listening Port
Detecting the presence of Trojan is a rather difficult action. The easiest way is to see which ports are open and are in a "listening" state, using certain utilities such as Netstat. This is because many Trojans run as a system service, and work in the background (background), so Trojan-Trojan is able to receive commands from the attacker from a distance. Examples of the use of the Netstat utility in Windows XP Professional: - Create a Snapshot
Another way that can be used is to create a "snapshot" of all program files (* .EXE, * .DLL, * .COM, * .VXD, etc.) and compare them over time with previous versions, in computer condition is not connected to the network. This can be done by creating a checksum of all program files (with CRC or MD5 or other mechanisms). Since Trojans are often loaded into directories where the operating system resides (\ WINDOWS or \ WINNT for Windows or / bin, / usr / bin, / sbin, / usr / sbin in the UNIX family), suspicious files are in that directory. Many suspicious files, especially program files that have similar names to "good" files (such as "svch0st.exe", should be "svchost.exe", a file that is run by many operating system services Windows) can be suspected as Trojan Horse. - Anti virus
The last way is to use an antivirus software, equipped with the ability to detect Trojans combined with a firewall that monitors every incoming and outgoing transmission. This is more efficient, but more expensive, since most antivirus software combined with firewalls has a higher price compared to the two ways above (which tend to be "free"). Indeed, there are some free tools, but it still takes time, effort and money to get it (download it from the Internet).