What is System Administrator??
1. Background
We’re going to discuss about System Administrator and what kind of applications they usually use. But, before that I’ll explain first about Information System. As we know that almost every organization and corporation especially the big one is using an information system to help their routine activity and help them to reach their goals. Based on Wikipedia, the Information System itself means an organized system for the collection, organizations, storage and communication of information.
But how important is this Information System for an organizations or corporations? Information System gain their importance by processing the data from company inputs to generate information that is useful for managing your operations. To increase the information system's effectiveness, you can either add more data to make the information more accurate or use the information in new ways.
Information systems are more than the computers. Effective usage of information system requires a thorough understanding of the organization, its management and the information technology it implies. Information system is defined as the "combination of hardware, software, infrastructure and trained personnel organized to facilitate planning, control, coordination, and decision making.”
After understanding about the relationship between an organization and Information System and also the importance of Information System in organizations, there is something that also important to be explored. The one behind the information system in organization. And that is what we are going to discuss in this article. It is the System Administrator. We will keep discussing about the System Administrator on the explanation below.
Kontributor:
Hasna Audita Rahma
2. Cloud Computing and Sysadmin
Cloud Computing is nothing but a large number of computers connected through the Internet/Wan. Cloud Computing is now part of technology and sysadmin must lean:
a. Automation software such as puppet, chef, etc.
b. Cloud infrastructure such as AWS, Openstack, etc.
c. Network service in cloud such as Content delivery networks (Akamai, CloudFront, etc.) and DNS servers.
d. Source Control
e. Designing best practices for backups and whole infrastructure.
3. What is so special about the system administrator account?
Many tasks for system administration can be automated using Perl/Python or shell scripts. For example:
a. Create new users
b. Resetting user passwords
c. Lock/unlock user accounts
d. Monitor server security
e. Monitor special service, etc.
4. Software that used by System Administrator for Windows
a. Windows Performance Monitor
The Windows Performance Monitor is different from the more straightforward Task Manager that you see when you right click the system tray. The Performance Monitor is rather more complicated to master, as it does so much. You can use it in conjunction with the Windows Resource Monitor to see what resources each program and process are using.
b. Windows Remote Server Administration Tools
This tool allows you to manage roles and features on remote servers. In other words, it lets you control what services are installed on remote Windows machines, since these are the roles and features being referred to.
c. Windows Power Shell
One thing the Windows Power Shell does especially well is provide Unix-like commands to the administrator. For example, it provides the ls command, just like Linux. Ls is an alias for the Power Shell command Get-ChildItem. Select-String is the UNIX equivalent of grep, except that it can also read the contents of files.
Like UNIX, you can pipe Power Shell commands to hook to one another, to make them much more useful.
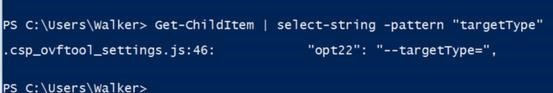
For example, you can search for files based on their name and, for text files, the contents of the file. The command below searches the current folder for any file that includes the string “targetType.” The string can be a regular expression or an ordinary string.
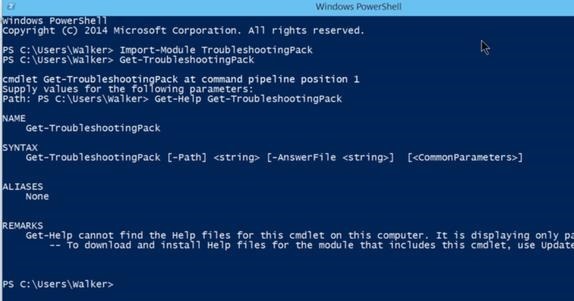
Windows Power Shell Troubleshooting Pack
The Windows power shell commands are called cmdlets. The cmdlets are specific to the systems administrator in the TroubleshootingPack module. You can ask it for instructions by typing:
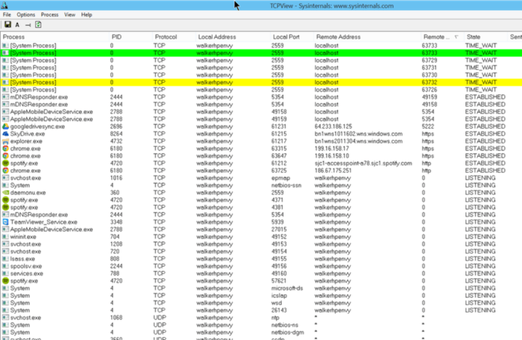
a. TCP View
TCP View is a tool provided by Microsoft that shows you what network connections each running program is making. This should be part of any system administrator’s toolkit to use as a means of auditing machines. You can look here to see if your computer is connecting to IP addresses you do not know, which could be a hacker. It also reveals what software is on your machine that you might want to remove since it is just taking up bandwidth and CPU without providing anything useful to you. Examples of this include Adobe update and many of the other update tools that vendors install without telling you.
b. WireShark
Wireshark is a packet sniffer tool. You cannot sniff network traffic from other machines on the network unless your routers are set up in promiscuous mode, which they will not be. But you can plug in a laptop to a router and see all traffic on the network. This is good for troubleshooting application issues. And it makes something which is otherwise relatively difficult to grasp (network traffic) more immediately understandable with a graphic interface.
c. Hyper V
Microsoft invented virtual machines and then VMware took over the market. So, most people use VMware Workstation. But you must pay for it. Hyper-V is included with Windows 2008 and Windows 2012. Use it for free for setting up a lab for troubleshooting or installing test versions of applications into a separate OS on your Windows machine. Other than that, you can use Oracle Virtual Box for free.
d. Windows Snare
Snare is a tool that outputs Windows event logs to a syslog server. Why is this important? Most intrusion detection and other logging systems process logs in syslog format, which is a UNIX format. Syslog is not a file, but a pipe. As such you can send the data to a syslog server, which reads it as if it were a file, except in real time.
e. Windows Process Monitor
The Windows Process Monitor is another tool from Microsoft. It gives you extremely detailed process information right down to which .dll a program is loading and which memory addresses these DLLs are loaded into. It looks at each step of a running program, so it generates millions of events per minute.
In the example below, you can see every registry key it has read, every file it has opened, created, or closed.
f. GFI Languard
GFI Languard is not a free product. It is, however, one of the better vulnerability and patch management tools. It also provides auditing tools. You’d characterize it as a system management and security tool. It scans for security patches and installs those that are absent. You can use it to push out software. sIt also works on Linux, so you could use the same tool for both platforms to standardize around a single tool.
g. Windows Reliability Monitor
The Windows Reliability Monitor is included in Windows 2008 and later versions of Windows. The red Xs in the screen show below show critical operating system events. You can click on the X to get detailed information drawn from the Windows event log. To run it type ‘reliability’ in the Start menu.