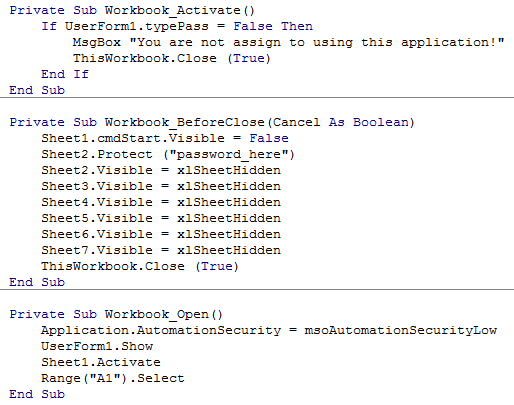
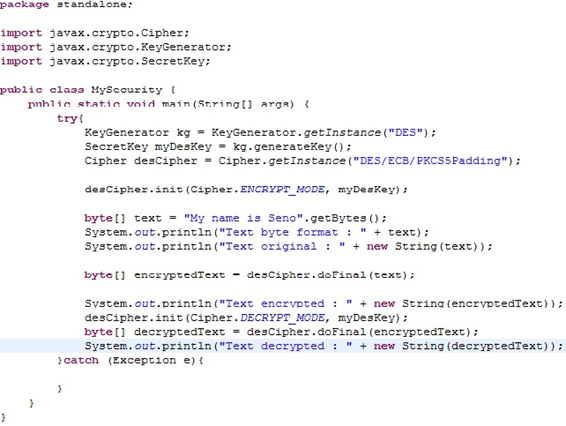
THE IMPORTANCE OF ENCRYPTION
Today, 90% of people use technology and the Internet to do everything, like learning, doing business, working, communicating, playing, taking vacations, sleeping sometimes using technology like listening to songs through mobile phones. That way, many important things or data contained in the technology. Since almost every human has entered the data in the technology, such as when creating a social media account, they must provide information about him / her (residence, age, mobile phone number etc) which is actually a privacy that must be maintained in common. If we are unaware of the security of our data, it will be bad, such as criminality or the other.
Especially for companies that certainly use various technologies in doing business. Many of the company's important data that should not be known by the outside pilak, and it is in need of strong security to ensure the confidential data is maintained.
Therefore, we as technology users should be able to ensure that our data is safe. Increasing number of hackers who can take personal data of someone or secret data company that is in the technology will be a threat to its users. This is why we should know about the encryption and apply it.
Kontributor:
Nia Titaning
Discussion
Encryption is the process of encoding or decoding or scrambling plaintext data in order to make it difficult for others to open the original data, except the intended party. While decryption is the opposite of the encryption, or the process to open the data in the encryption by using private key.
The advantages of Encryption
- Confidentiality of information is assured
- Provide authentication and protection
- Tackling phone tapping and email
- For digital signature
Disadvantages of Encryption
- The encoding of a terrorist plan.
- Hiding criminal records by a criminal.
- The message can not be read if the message recipient forgot or lost the key
Encryption has three categories:
- Secret Encryption Key (Symmetric Encryption), meaning a key that can be used to encrypt and decrypt data at once.
- The algorithm will break the data into small pieces or so-called blocks. Then dig the letters and change the information in the block into a number and increase the size of the data, then run it with a mathematical formula. This can be repeated until repeatedly.
- Symmetric encryption is very easy and fast in use, but the security level is not as strong as asymmetric encryption, because the private key will be given to the recipient to decrypt or open data sent by the sender. Therefore, other people can decoding the data, because they already know the private key.
Public Encryption Key (Encryption Asymmetric), meaning there are two keys that each function to encrypt and decrypt data.
The algorithm used in this asymmetric encryption treats the letters into a very large number and multiplies them into larger numbers which then calculates the rest after being shared with the other third largest number. Finally, this leftover number is converted back into a text.
Asemetric encryption is more complex than symmetric encryption, but more secure. In asymmetric encryption, there are two different keys, namely the private key and the public key that will be given to the recipient to decrypt or unlock the locked data. This public key can only be used for coding data, but not for decoding data. Others send the encrypted data with the public key we provide, and we can open it with the private key we have. As for the private key will be safe to us, because the private key is not given to anyone.
One-way Function, a function where information is encrypted to create a "signature" of the original information that can be used for authentication purposes.
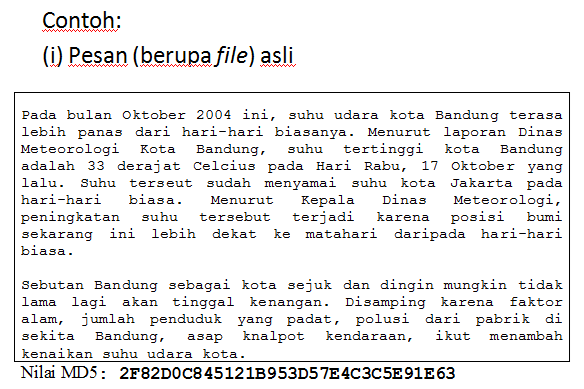
Sample case :
we have documents that will be sent to someone or save for us to open a time, we can use a one-way function technique that will generate a value with a certain length called a hash. Hash is a unique signature of a document in which we can put or transmit along with our documents. The message recipient can run the same one-way function to generate another hash. Furthermore the hash is mutually compared. Where appropriate, the document can be returned to its original form.
· Application of one-way function
- Maintain data integrity
o The hash function is very sensitive to 1 bit changes in messages
o Message changed 1 bit, hash value changed very significantly.
o Compare the new hash value with the old hash value. If the same, the message is still original. If not the same, the message has been modified