CASE OF COMPUTER FRAUD IN BUSINESS ENVIRONMENT
Kontributor:
Fatikhah Geya
Definition Computer Fraud
A computer is an electronic device used to process data or information according to a defined procedure
Fraud is a disadvantage committed by a person or a group of people to benefit unjustly from other parties. Fraud can happen anywhere and anytime, fraud can be done by insiders who know all data and information owned by the company (internal fraud), and can also be done by outsiders, but fraud by outsiders will be difficult because a company certainly have had a security system to keep their data and assets.
Computer fraud is the use of computer technology by a person or group of people for fraudulent acts. Examples of computer fraud actions are copying, modification, access, theft of corporate data, and illegal information retrieval.
Nowadays computer fraud occurs mostly from the irresponsible people, they just want to make a profit regardless of how they do right or wrong. This is of course very worrying and disadvantageous for us, to reduce the risk of computer fraud required precise prevention and serious supervision, if not handled seriously it will be very dangerous because it can cause losses that very much even can lead to bankruptcy.
Computer fraud is done with high technology that is difficult to detect, to detect it we can use software such as CAAT (Computer Assisted Audit Tools), with this tool auditors can be easier to uncover cyber crime through computer fraud, auditors who will audit the cyber crime must be experts in EDP audit and fraud audit. Currently we should be able to develop the science of computer forensic, because cyber crime through computer fraud increasingly sophisticated and widespread.
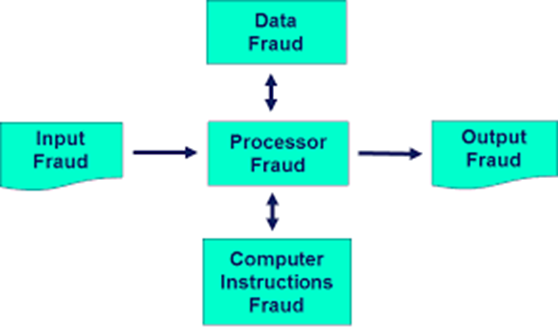
Computer fraud can be classified into 5 and can be categorized using the data processing model
- INPUT FRAUD
Fraudulent actions by changing computer input - PROCESSOR FRAUD
Theft of time and services included in the processor fraud, for example are employees who waste time and use the internet for personal use during working hours - COMPUTER INSTRUCTION FRAUD
Included in the computer instruction fraud is the act of destruction of software to process corporate data - FRAUD DATA
The act of altering, destroying, copying, and using unauthorized corporate files - OUTPUT FRAUD
The output data usually displayed on the screen is usually an easy material for spying
Factors that cause increased computer fraud:
- many actions of computer fraud that is not detected, or already detected but not reported
- many networks that the security level is still low and easy to break
- many ways or instructions to start the action computer fraud available on the internet and easy to get
- calculating losses is difficult
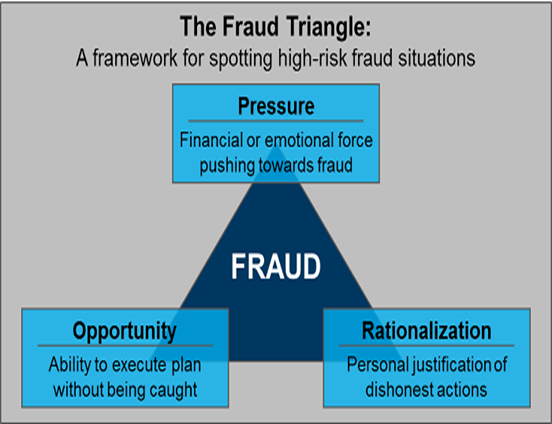
Pressure: a person's financial condition is weak or unstable, and lifestyle can encourage the actions of computer fraud. Pressure is divided into two forms: real (direct) and perception (indirect), examples of real pressure are pressures arising from daily life problems faced by the perpetrator, and examples of perceptions of pressure are the opinion of the perpetrator who encourages fraud eg executive need
Opportunity: an opportunity that causes the perpetrator to commit fraud freely, this opportunity can arise because of weak control system owned by the company, so the perpetrator can make fraud easily
Razionalization: the attitude of the offender seeking justification for the act of fraud, for example
- employees who feel they have worked long enough and deserve to get a higher position and salary
- an employee who feels his company has gained so much profit that it does not matter if he takes a little of the company's profits
Examples of actions included in computer fraud
- commit fraud with incorrect document input, such as entering the purchase order data, acceptance reports, and supplier invoices that never happened
- making software tools that use the computer's active time in the company to be sold commercially by the programmer
- use and steal other people's internet accounts, usually victims of this incident do not feel any objects stolen, the effect of this incident will be felt if the information stolen is used by unauthorized persons
- the Cyber Crime E-Commerce case in Indonesia that falsified letters and documents relating to business
Various examples of computer fraud cases in the business environment
- Carlos Slim, the world's richest person exposed to cybersquatting. Cybersquatting is registering, selling, or otherwise using another person's domain name to take advantage of the trademark or the name of the person who is already famous for resale. Domain owned by Carlos Slim carlosslim.com successfully snatched by others with a mode to trade the popularity that has been owned by the company and keyword Carlos Slim by selling google ads to its competitors. Luckily this case can be resolved by the Anticybersquatting Consumer Protection Act (ACPA) procedure, this procedure entitles the trademark owner to sue the cybersquatter in federal court and transfer the domain name back to the trademark owner, in some cases the cybersquatter has to pay compensation in the form of money as sanctions.
- The ANTV website (one of the broadcasting companies in Indonesia) was exposed to Deface on Thursday (12/11/2009). Deface is a technique for replacing or inserting files on a server that usually lacks its security system in an application. Deface is done to change the look of the website. The ANTV site gets deface on the inside of the site, so it looks okay when viewed from the front view, but when searched deeper, on a page no visible information or news whatsoever, the hacker just writes runnig text "hacked by james0baster", and on another page is written "hacked by bejamz" with the look of "newbiw deace crew" as well as two cartoon images of Mario Bros.
- PT Semen Tiga Roda was hacked by hackers on the week (14/12/2008), hackers deface the pages of PT Semen Tiga Roda's website, the site display becomes black with a hacked writing that is formed image of a skull, hackers also write "Cell website has been hacked by: AGIZ Touch Your Site Greetz: Evi as My lovely gurl ^ - ^ ", not only that, hackers also dare to leave his email on send mail message to: gembelmuda@ymail.com". The reason the hackers attacked the site of PT Semen Tiga Roda is allegedly due to the increasing public protests against the plan to build a factory of PT Semen Gresik in the mountains kendeng, Central Java.
- The CarWise ICT software company was successfully burglarized on August 7, 2017, the incident was discovered by the ESET security company. It is estimated that at least 100,000 data have been successfully stolen.
The incident was found on LeaseWise software, which was used by 52 Dutch car rental companies. Companies share their data base, but because of leakage then the data base can be accessed by other parties. Leaked data includes customer addresses, rental contracts and the number of kilometers traveled per car. This incident may be closed within 24 hours after being notified by ESET.
As early as 1979, time magazine labeled computer fraud a "growth industry". today many businesses are victims of computer fraud. Recently, a spy network in china hacked into 1,300 government and corporate computers in 103 contries. The perpetrators do computer fraud with a very sophisticated, and this incident resulted in enormous losses.
Prevention that we can do to reduce the occurrence of computer fraud
- protect important data with a variety of existing applications to enhance corporate protection
- make employment confidential agreements
- create a special oversight body to safeguard the company's important files
- personnel sreening
- segregration of duties
- professional ethics
- physical access security
- electronic access security
- internal control and edit